Hassan (06-01-2010)
Results 1 to 15 of 16
-
05-31-2010 #1
How to: protect your application - License , HWID Lock & Much more!
How to protect your application!
Written by Soul Collector
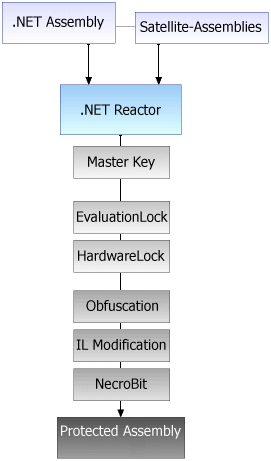
.NET Reactor


Download from the official website.
https://www.eziriz.com/
.NET Reactor is also great tool against the scammers & leechers.You can add custom license to your program without adding any code in your program, also you can HWID lock the software. I highly recommend this tool
Intellectual property protection
- NecroBit Protection
- Native Code generation
- Obfuscation
- Control Flow Obfuscation
- String Encryption
- Anti Tampering
- Resource Encryption and Compression
- Dependency Merging
- Protects full applications and libraries (dlls)
Powerful licensing system
- Create trial versions of your software
- Set an expiration date
- Limit use to a fixed number of days after installation
- Limit by number of uses
- Limit to use for no more than a set number of minutes each invocation
- Limit trial version functionality
- Easily turn your trial version into a fully licensed version
- License your software
- Permanently (non expiring license)
- By time period (i.e rent your software)
- By number of uses (i.e software as a service)
Software development kit
- Integrate license checking into you assembly and extend licensing fuctionality
- Extend licensing functions with bespoke extensions.
Why you need to protect your intellectual property.
When you compile a program written for the Microsoft .NET framework, the program you provide to your users is not compiled into a native executable program, but instead is translated into something called the Common Intermediate Language instructions (CIL). CIL is half way between source code and native code, and is interpreted by the .NET framework when your program is run, rather than executed directly as machine code. Because of this, the source code of your application or library can be easily reproduced. Tools such as .NET Reflector (.NET Reflector, class browser, analyzer and decompiler for .NET) can reproduce source code from a compiled .NET assemblies in seconds, and in the .NET language of your choice! Clearly, commercial software distributed to end users without some form of protection is wide open to piracy and intellectual property theft.
The traditional solution to intellectual property protection in .NET is to use 'obfuscation', indeed Microsoft make an obfuscation utility available to Visual Studio users.
So why is obsfucation not enough?
Obfuscation is the process of making your source code more difficult (but not impossible) for humans to understand. Obfuscation works by replacing the meaningful names you assign to classes, methods, properties and variables with meaningless ones. For example, it may replace a variable name of "counter" with "A4DF3CV89G" - to humans these obfuscated names are confusing and difficult to remember, but have no effect on the NET Framework interpreter. Note that obfuscation does nothing to the source code within your methods, so it is not protected at all by obfuscation. .NET Reactor does everything an obfuscator does, but then wraps your intellectual property in several more layers of protection, denying access to your source code to even those who are determined to steal your hard work. .NET Reactor's protection has never been cracked, something which cannot be said about obfuscators.
Industry Leading .NET Reactor Source Protection
.NET Reactor prevents decompilation by a variety of methods which convert your .NET assemblies into processes which no existing tool can decompile ( and which are also very likely to prevent decompilation by any future tool). .NET Reactor builds a native code wall between potential hackers and your .NET assemblies by producing a file which cannot be understood directly as CIL. Because the CIL in your assembly is emitted intact only at run time or design time (in a form in which the source is completely inaccessible), no tool is capable of decompiling .NET Reactor protected assemblies.
The native code wall created by .NET Reactor between the hacker and your source includes industry leading NecroBit technology, which is exclusive to .NET Reactor. .NET Reactor's protection has never been broken since the first release in 2004. These technologies make reconstruction of your source code more difficult by so many orders of magnitude that NecroBit is by far the most effective protection you can use for .NET assemblies.
In addition to industry leading intellectual property protection, .NET Reactor provides powerful options for securing you revenue stream by enforcing licensing terms with a rich variety of trialversion and full version locks.
NET Reactor offers you simple and reliable ways to:
- Secure your .NET applications and .NET libraries
- Replace CIL code with native code
- Perform additional layers of protection, including obfuscation
- Merge assemblies, and
- Protect your revenue by enforcing trial version restrictions and full version licensing terms.
The protection mechanism is so simple you can download and install .NET Reactor, and produce your first truly protected .NET assembly in minutes, without any changes to your source code.
Supported Platforms : Windows 98, Windows ME, Windows NT, Windows 2000, Windows XP, Windows 2003/2008, Windows Vista, Windows 7
Supported Platforms (Mono) : Linux - SUSE, Novell, Red Hat, Mac - OS X 10.3, 10.4, Solaris 8, BSD - OpenBSD, FreeBSD, NetBSD
Last edited by Ian; 05-31-2010 at 02:27 PM.
-
The Following User Says Thank You to Ian For This Useful Post:
-
05-31-2010 #2
Thanks for sharing this whole bunch of information.

-
05-31-2010 #3
is this outside link allowed?
-
05-31-2010 #4
I don't understand this.
How do you make the serial key for your program?
-
05-31-2010 #5
-
05-31-2010 #6
Do you have a license key to register the product?

-
05-31-2010 #7
-
06-01-2010 #8
Very helpful, thanks for sharing mate


-
06-01-2010 #9
Uhm. Could be better if you told us HOW to use it?

-
06-01-2010 #10
-
06-01-2010 #11
I think he told us how to do it. See the pictures he added to his post. He highlighted what to do.

-
06-01-2010 #12
Yeah but, it doesn't tell you what to do after that.
Anyway whats a Hardware ID =.=
-
06-01-2010 #13
-
06-01-2010 #14
Easily to figure out I'd say. It's annoying that I dun have a license though.

-
06-01-2010 #15
Similar Threads
-
[Source Code] How to Protect your dll ( Hack )
By Qmo in forum Coders LoungeReplies: 26Last Post: 08-16-2012, 11:08 AM -
How to protect your self from the ring.
By zatchbell3 in forum GeneralReplies: 7Last Post: 06-12-2011, 03:29 AM -
How To Utilize Text to Speech in your application
By GG2GG in forum Visual Basic ProgrammingReplies: 3Last Post: 10-10-2009, 01:42 PM -
How to protect your account information on anywhere from anyone
By BARON in forum Combat Arms Hacks & CheatsReplies: 0Last Post: 04-09-2009, 05:18 PM -
How big is your gun? o.-
By SadisticGrin in forum Art & Graphic DesignReplies: 10Last Post: 08-01-2006, 09:58 PM


 General
General


















